How To Reveal A Windows Services Password
In our "pretend pentest" that we've been running these last few days, we've now got all the domain admins listed, all the service accounts plant and listed, and the intersection of those 2 things - the service accounts that are either local admin or domain admin.
So what's the obvious next pace? Let'due south recover the passwords for those target service accounts! Because once nosotros have the full credentials, we have admin rights that no SEIM or systems admin will exist tracking the employ of - these accounts are almost universally ignored, since they login every fourth dimension those services start (say during a system restart). And then if this is for instance a service account with domain or local admin rights that's on every server and workstation, you are now "amend than domain admin". You lot take all the rights, but no system controls are watching you!
Let's get on with the chore at hand.
First of all, credentials for service accounts are stored in the local registry, equally what'south called "LSA Secrets" in the registry cardinal HKEY_LOCAL_MACHINE/Security/Policy/Secrets. Considering the service needs to read the bodily countersign to login equally the service business relationship, that password is in the registry in clear-text. Yup, you read that right - this is why service accounts are such a great target. LSA Secrets are well protected all the same, you can't merely fire up regedt32 and read them - only the SYSTEM account has rights. And then you need ... yes, some powershell! Not only that, many of today's tools are based on some powershell posted way dorsum in the solar day on microsoft.com!
https://gallery.technet.microsoft.com/scriptcenter/Enable-TSDuplicateToken-6f485980
https://gallery.technet.microsoft.com/scriptcenter/Get-TSLSASecret-9bf94965
(Thanks TrueSec!! In fact, thanks from all of us! )
Or if yous're not in the mood for PowerShell, you lot could use some Python tools, or Metasploit or Mimikatz works too - choose your own run a risk! Often you lot'll need to try a few unlike methods, and then maybe wrap i in some "AV evasion" code to make it piece of work for y'all, but the results are worth it in the end!!
Nishang
Those original scripts from microsoft don't work on mod hosts with any patches applied at all, but of class at that place'southward a toolkit that'south improved on these scripts over fourth dimension. I mostly use Nishang for the PowerShell-centric "I'm on the box" approach to LSA Undercover recovery
Nishang can run locally on the Windows host being targetted, or you can of course use PSRemoting. The problem with this tool is that if there's an AV product in play anywhere in the chain, it will very likely accept a trouble with you running Nishang. In fact, fifty-fifty downloading this on a Windows host with a default install (ie - with W10 Windows Defender in play) can be a problem.
Anyway, once information technology's installed, the execution if pretty straightforward:
> Import-Module .\nishang\Gather\Get-LSASecret.ps1
> Import-Module ./nishang/Escalation/Enable-DuplicateToken.ps1
> Enable-DuplicateToken
> Get-LSASecret
Name Account Secret ComputerName
---- ------- ------ ------------
...
...
_SC_Service Proper name Being Targeted .\SVCAccount Passw0rd123 ComputerName
Metasploit
Metasploit of grade has a module for this. Yous can run it locally or (more probable) remotely. The module is post/windows/gather/lsa_secrets.
Because endpoint protection programs tend to focus so much on Metasploit (which of course tells us just how good this tool is), you lot demand to be careful where and how you run it if the goal is to get this job done with any caste of stealth. Y'all'll want to put some up-front piece of work into evading whatsoever your customer has for AV - this work pays off in all kinds of ways if the pentest you're running is longer than a few days. This method does a not bad job though, even though (depending on the module you're running) it'll tend to scream at the AV solutions "Await! Look at me! I'm running Metasploit!"
The MetaSploit method is a simple as "run postal service/windows/gather/lsa_secrets"
For me the most attractive thing about using Metasploit is that yous can script the exploits. And then if y'all need to, you tin run 4-5-6 exploits against hundreds of machines in i go.
Dumping LSASS
You tin can dump the LSASS process retentiveness and recover service passwords (and a ton of other stuff too) from that, but that becomes less and less reliable over time equally Microsoft puts more fences and protections around LSASS. I've never had to go this manner on a real date. The easier method is to run the MimiKatz PowerShell Module and only sentry the magic happen. That is if you put the work into evasion against your endpoint protection solution to allow MimiKatz to run.
Impacket
Impacket makes a bang-up little python based tool to attain the same matter. This is my kickoff, go-to, it most ever works method - mainly considering all you run on the target host is standard windows commands, and then the rest of the set on is on the assaulter'due south host. This makes it the to the lowest degree likely of these methods to trigger whatever AV alerts or other security measures.
First, from the local host we dump the 3 registry hives that are in play:
reg save hklm\sam sam.out
reg salve hklm\security security.out
reg salvage hklm\system arrangement.out
Now accept those files and get thee to your Kali VM! If you lot don't have impacket installed yet (information technology'south not in the default install), there'south no time similar the nowadays. To install:
$ sudo apt-get install python-dev python-pip -y
$ pip install --upgrade pip
$ sudo pip install pycrypto pyasn1 pyOpenSSL ldapdomaindump
$ git clone https://github.com/CoreSecurity/impacket.git
$ cd impacket
$ sudo python setup.py install
(in near cases yous don't need all of those pre-reqs, I put them all in simply in instance). Now you're good to go:
impacket-secretsdump -sam ./sam.out -security ./security.out -organization ./system.out LOCAL
(y'all'll find a bunch of other interesting security stuff in this tool'southward output - all the local business relationship password hashes for one thing!)
At the bottom of the output, you'll see what nosotros're looking for, the locally stored password for that service account!! In this example I put a "fake" account on my SFTP server service (Solarwinds SFTP doesn't have a service account by default).
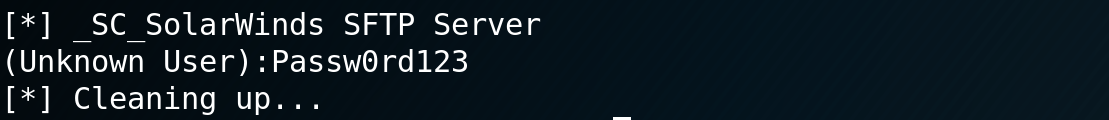
That'southward it - no fuss, no muss, and all-time of all, nothing to trigger AV or any similar "endpoint next-gen auto-learning AI user behavioural analysis security" product on the target host.
Other tools like CrackMapExec practise a skillful job every bit well - I haven't used that i specifically nevertheless, really the impacket method has done the chore for me and so far. While I tend to have a "attempt 1 or 2 new things" or "write one new tool" dominion for each exam, I haven't gotten around to using any other tools for this particular matter.
Do you lot utilise a different tool to dump service passwords? Does your tool collect more than useful data than just that particular affair? Or maybe you've got a cool AV evasion that relates to this? Please, use our comment form and share your experiences on this!
=============
Rob VandenBrink
Compugen
573 Posts
ISC Handler
Apr 26th 2019
Came across this on Reddit last night - pull the local NTLM hashes via powershell. It'due south concise enough to be pasted into a powershell session, in all likelihood avoiding the ire of AV..
https://github.com/off-earth/NTLMX
How To Reveal A Windows Services Password,
Source: https://isc.sans.edu/forums/diary/Pillaging+Passwords+from+Service+Accounts/24886/
Posted by: johnsensterst.blogspot.com


0 Response to "How To Reveal A Windows Services Password"
Post a Comment